Sym3 Authentication and Authorization Service
The Sym3 Authentication and Authorization Service (Sym3 Auth Service) server is a service to facilitate user and resource authorization using the industry standards OAuth2 and Open ID Connect (OIDC). OAuth 2.0 (Open Authorization), is a standard designed to allow a website or application to access resources hosted by other web apps on behalf of a user. It’s now the industry standard for online authorization.
All Sym3 Operator web Apps and APIs are secured by the Sym3 Auth Service.
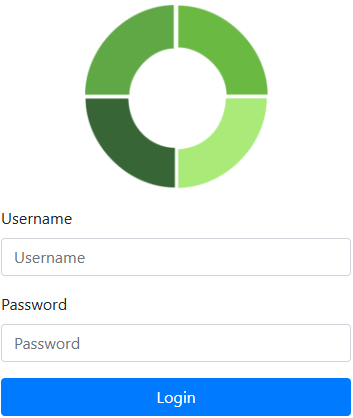
User login
Sym3 Web redirects all login requests to the Sym3 Auth Service. The login page displays different login buttons depending on the authentication method configured in the Settings page.
| Basic Authentication | Active Directory | Azure Entra ID |
|---|---|---|
 |
 |
 |
Active Directory Authentication
The Active Directory Authentication (AD Auth) mode works when the Sym3 Auth Server is hosted on a computer that is part of a Windows domain.

The ‘Use Active Directory Groups’ option is enabled by default. User roles will be mapped automatically from the AD groups. In this mode, administrators cannot add AD users from the Users page. If the option is disabled, users with an AD account must be added to the Users page by the administrator first. The administrator will then need to assign roles manually.
The domain name must be configured in the domain name field. If the configuration is missing, the field will be automatically filled with the domain detected by the Sym3 Auth Server. Click the ‘TEST CONNECTION’ button to validate the domain name.
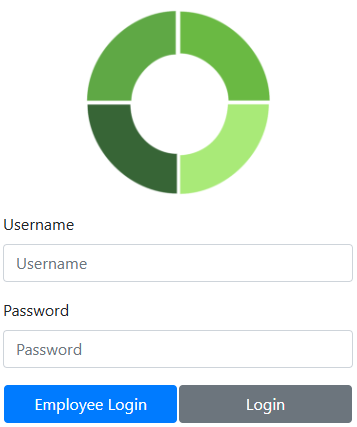
The login page will display an Employee Login button if the Active Directory Authentication mode is selected.

Enter the AD username and password, then click the Employee Login button to validate the credentials with the AD server and log in.
Basic authentication user accounts still work in AD Auth mode. Enter the basic username and password, then click the Login button to log in.
Azure EntraID Authentication
An Azure application must be registered before the Sym3 Auth Server can operate in Entra ID mode. Get more information from the Azure EntraID Configuration page
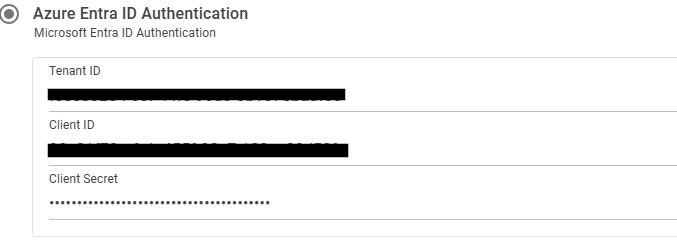
The tenant ID, client ID, and client secret can be found on the overview page of the application registration in the Azure portal.
The tenant ID is highlighted in red and the client ID is highlighted in orange.
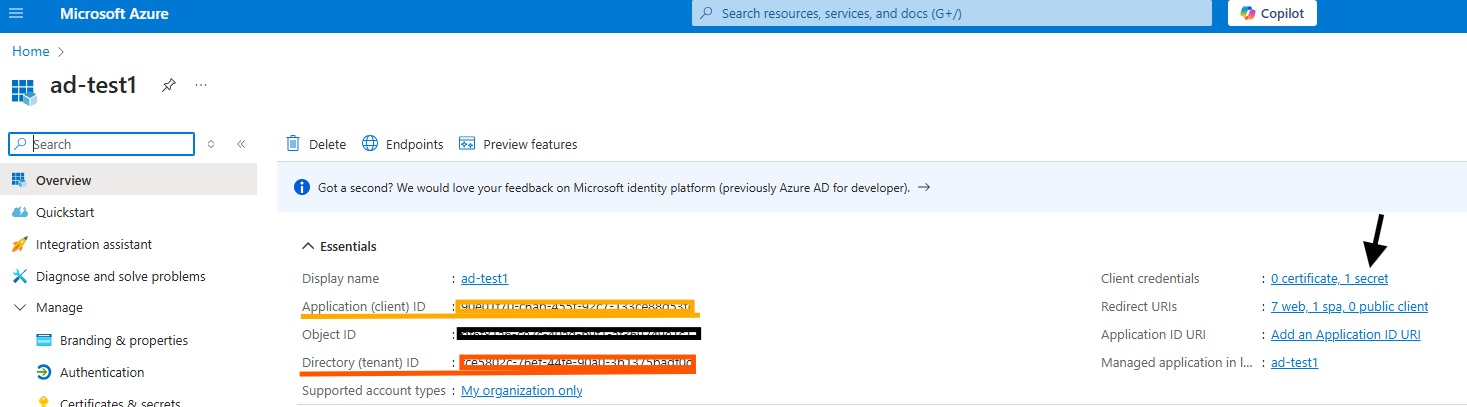
The client secret is located in the Certificates & secrets page. Click the link pointed out by the arrow page. Client secrets are visible immediately after creation. If the value was not stored, simply create a new one.
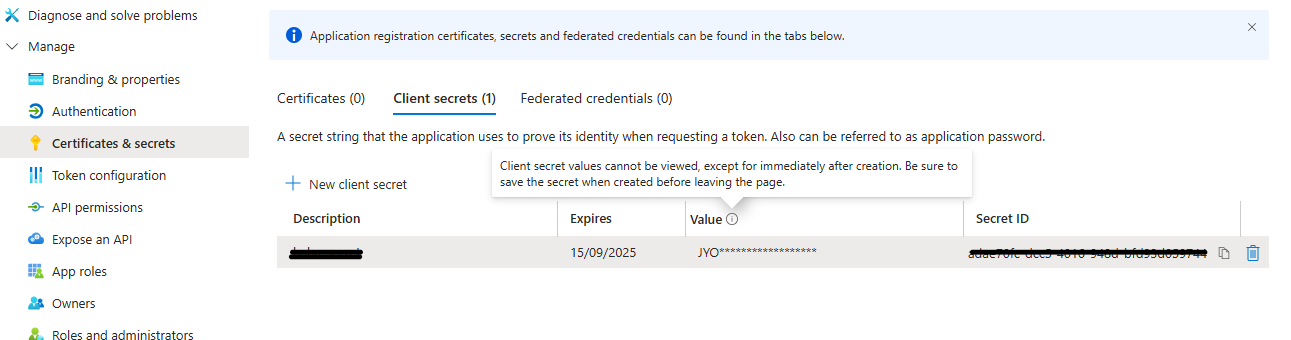
EntraID mode map the user roles from the user group IDs. Get the user group IDs from Azure portal.
Restart the Sym3 Auth Server to apply the changes.
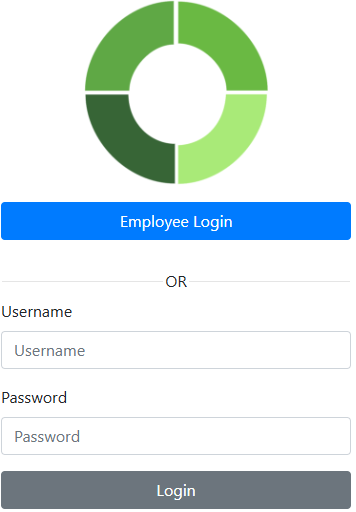
The login page will display an ‘Employee Login’ button if the ‘Azure Entra ID Authentication’ mode is selected.

Click the ‘Employee Login’ button to be redirected to the Entra ID login page.
Users may receive a validation request on their mobile phone or email, managed by the customer’s IT department.
Basic authentication user accounts still work in Azure Entra ID mode. Enter the basic username and password, then click the ‘Login’ button to log in.
Project Role Mapping
User roles can be mapped from the groups of external identity providers.
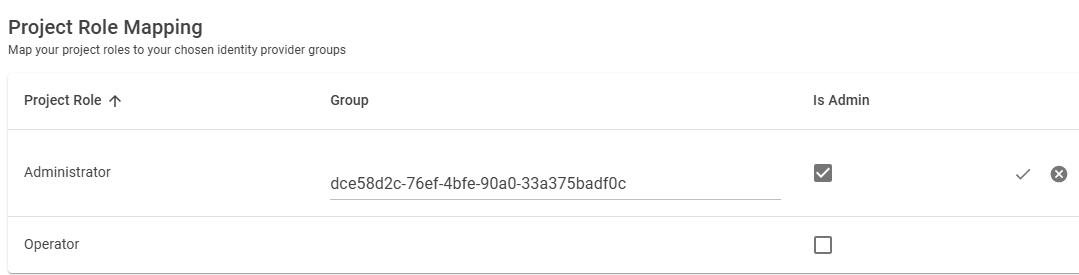
The project roles are from the active project and can only be updated in the Sym3 Operator Editor. The ‘Group’ column represents the external identity provider’s group.
- For Active Directory, a typical group name looks like ‘NORTHWIND/SYM3_Administrator’. Check with the AD administrator for the available group IDs.
- For Azure Entra ID, the values are the GUIDs of the groups.
