Settings
The settings page allows users with the PlatformAdmin role to manage how all services are operating.
To access the settings page, click the “Settings” link in the left navigation menu. If you do not see it, click the triangle next to the “Administration” link. If the “Administration” link is not present, double check that the user you are signed in as has the PlatformAdmin role.
All settings available:
- Operator Server Settings
- Alarm Server Settings
- Auth Server Settings
- Replay Server Settings
- Web Client Settings
- Certificate Management
- License Settings
Operator Server Settings
Once all desired Operator server settings modifications are made, click the save button on the bottom of the screen. The Operator server must be restarted for settings to take effect.
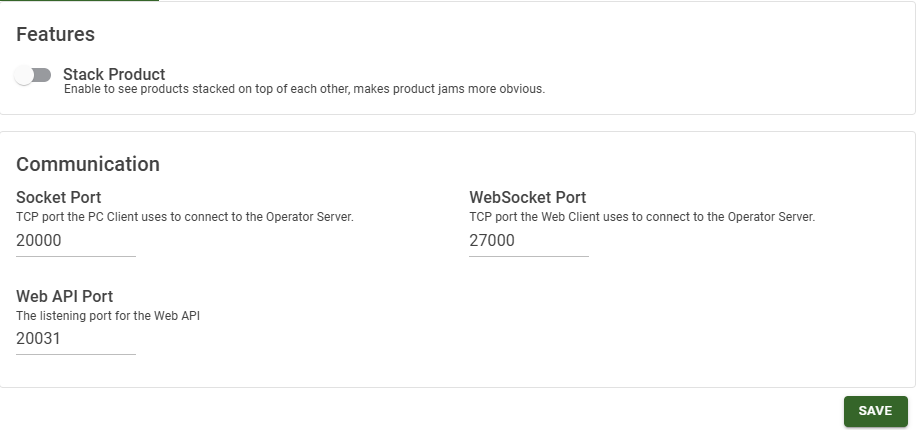
| Setting | Description |
|---|---|
| Stack Product | Default = Disabled Enable this if you need to see products stacked on top of each other rather than appearing as if they are one box. This makes a product jams more obvious as a tall stack of boxes. |
| Socket Port | Default = 20000 The port the PC client uses to connect to the Operator Server. |
| Websocket Port | Default = 27000 The port that the web client uses to connect to the Operator Server. |
| Web API Port | Default = 20031 The port for the RESTful API. |
A Note On The Secure Websocket
Since version 10, the Sym3 Operator only has the secured WebSocket open. A secure websocket needs to be bound to a certificate. This can be done from the command line (the terminal must be run in Administrator mode) by typing this command: netsh http add sslcert ipport=0.0.0.0:[websocket port] certhash=[your certificate thumbprint] appid=’{6228e9d3-375a-4856-91a5-d195127299b3}'
netsh http add sslcert ipport=0.0.0.0:27000 certhash=f5579deba1fbc92a07386c5d8ff3cf4ce0c95f64 appid='{6228e9d3-375a-4856-91a5-d195127299b3}'If the referenced certificate is self signed or deemed invalid by the browser (the web client cannot connect to the websocket), open the following URL in a new browser tab and select the ‘Advanced->Proceed’ option to the certificate warning: https://localhost:[websocket port]
Example:https://localhost:27000
Alarm Server
The alarm server settings are split into several sections. Once all desired alarm server modifications are made, click the save button at the bottom of the screen. The alarm server must be restarted for settings to take effect.
Database
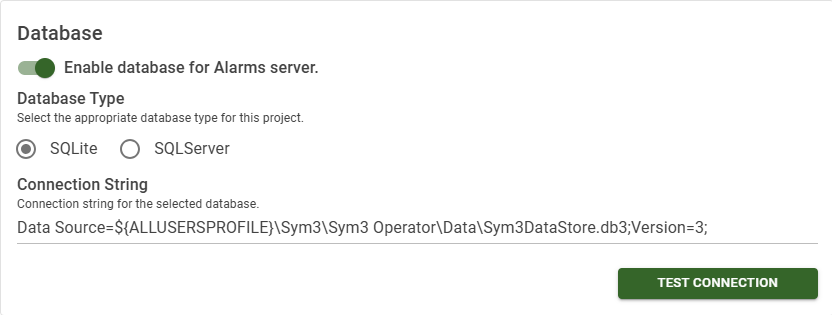
Uncheck the check box in the top right to disable logging to the database entirely.
| Database Type | Default Connection String | Notes |
|---|---|---|
| None | Has the same effect as disabling the database. | |
| SQLite | Data Source=${ALLUSERSPROFILE}\Sym3\Sym3 Operator\Data\Sym3DataStore.db3;Version=3; |
The variable ${ALLUSERSPROFILE} is C:\ProgramData on a a standard Windows install. |
| SQLServer | Server=localhost;database=DATABASE_NAME;Integrated Security=SSPI; |
Replace DATABASE_NAME with the correct name of the database to use. |
Features
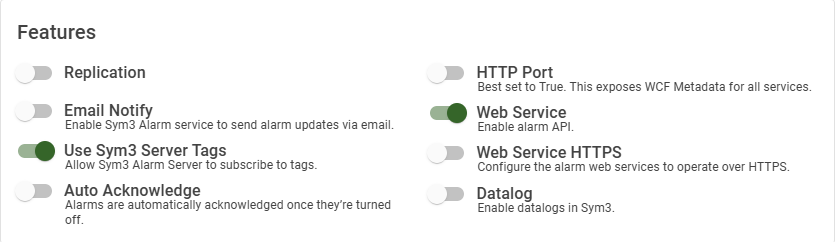
| Setting | Description |
|---|---|
| Replication | Default = Disabled Slated for evolution. |
| HTTP Port | Default = Disabled Enable an HTTP access point used by legacy mobile clients. Not used by the web client. |
| Use Sym3 Server Tags | Default = Enabled Allows the Alarm server to subsrcibe to tags. |
| Email Notify | Default = Disabled Enables the Alarm server to send alarm updates via email. |
| Web Service | Default = Enabled Allows the web client to use the experimental alarms reading API. |
| Auto Acknowledge | Default = Disabled Slated for evolution. |
| Datalog | Default = Disabled This must be enabled if datalogs in Sym3 are to be used. |
| Web Service HTTPS | Default = Disabled Makes the web service the web client communicates with use HTTPS instead of HTTP. If you’re using a secure endpoint to access the web client, this should be set to true. |
Event Service
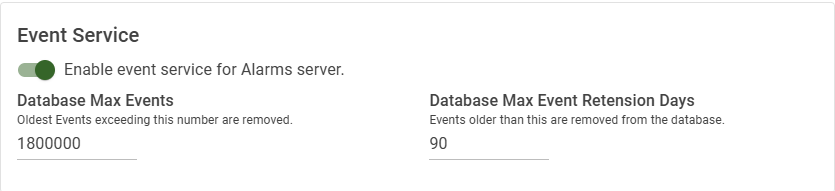
Uncheck the check box in the top right to disable the event logging service.
| Setting | Description |
|---|---|
| Database Max Events | Default = 1800000 As new events arrive, the oldest events in excess of this number are removed from the database. |
| Database Max Event Retension Days | Default = 90 days Events older than this are removed from the database. |
Maintenance
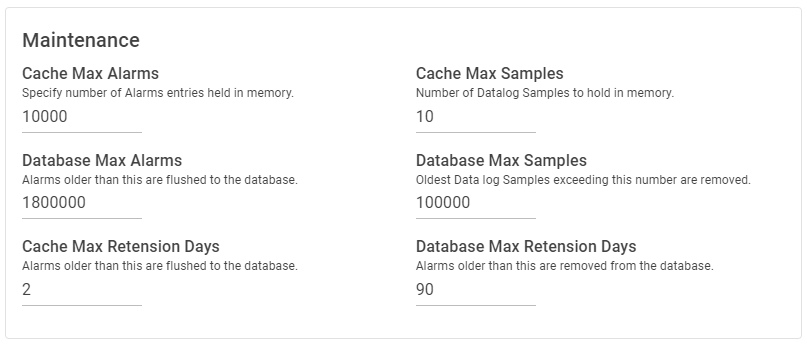
| Setting | Description |
|---|---|
| Cache Max Alarms | Default = 10000 Specify number of alarms entries held in memory. These are stored in a queue with older alarms written to the database as new ones arrive. |
| Database Max Alarms | Default = 1800000 Oldest alarms exceeding this number are removed from the database as new alarms arrive. |
| Cache Max Samples | Default = 10 Number of datalog samples to hold in memory. Older datalog samples over this value are written to the database. |
| Database Max Samples | Default = 100000 As new samples arrive, the oldest datalog samples exceeding this number are removed. |
| Cache Max Retention Days | Default = two days Alarms older than this are flushed to the database. |
| Database Max Retention Days | Default = 90 days Alarms older than this are removed from the database. |
Communication
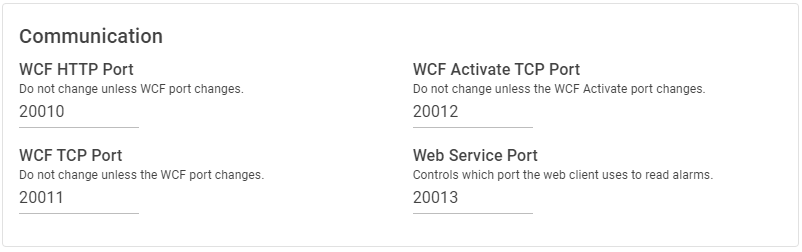
| Setting | Description |
|---|---|
| WCF HTTP Port | Default = 20010 Do not change unless WCF port changes. |
| WCF Activate TCP Port | Default = 20012 Do not change unless the WCF Activate port changes. |
| WCF TCP Port | Default = 20011 Do not change unless the WCF port changes. |
| Web Service Port | Default = 20013 Controls what port the web client reads alarms through. |
Auth Server Settings
The Sym3 Authentication and Authorization Server supports following authenticators:
- Basic Authentication
- Active Directory Authentication
- Azure Entra ID Authentication
Click the Save button at the bottom of the screen after making the changes. Restart the Auth Server to apply the latest settings.
Get more information from the AuthServer Settings page
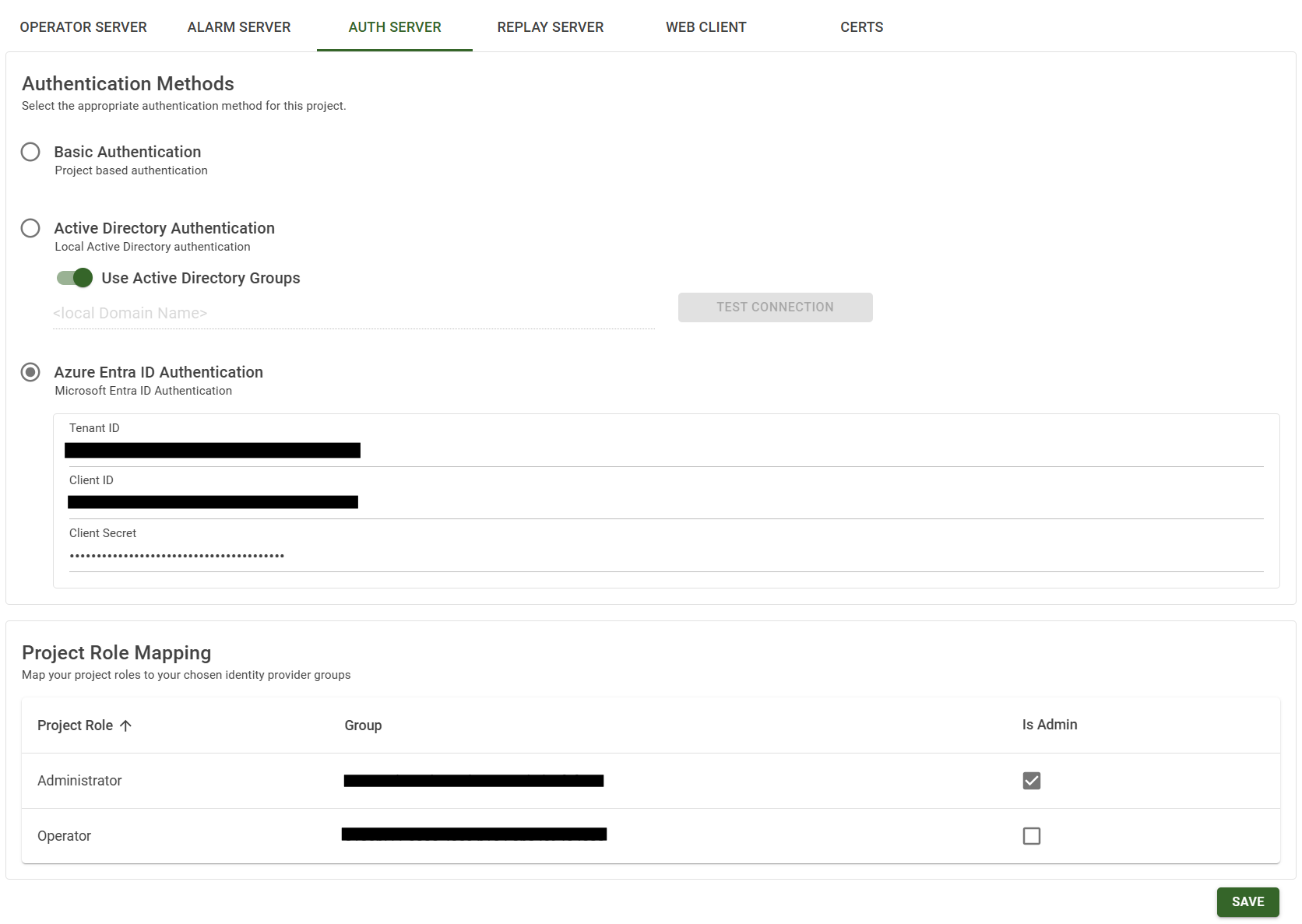
| Setting | Description |
|---|---|
| Basic Authentication | In the ‘Basic Authentication’ mode, the user records are stored in the Auth Server database. |
| Active Directory Authentication | In the ‘Active Directory Authentication’ mode, the user details are retrieved from the connected Active Directory server. |
| Azure EntraID Authentication | In the ‘Azure EntraID Authentication’ mode, the user details are retrieved from registered EntraID account. |
| Domain name | The domain name of the Active Directory. The ‘Test Connection’ button can be used to test domain accessibility. |
| Role mapping | Mapping between project roles and Azure EntraID group names. |
Replay Server
Replay Server settings are used by the Replay service. They are grouped into three sections:
- Recording
- Replay
- REST API
Recording
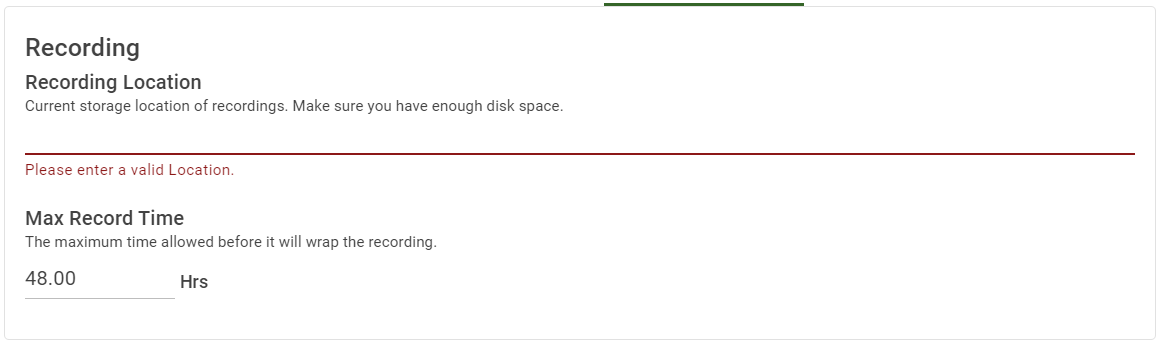
| Setting | Description |
|---|---|
To enable/disable Replay feature.
|
|
| Default = Empty Current storage location of recordings. It is a required field. |
|
| Max Record Time | Default = 48 hours (2 days) The maximum number of hours allowed before it will wrap the recording. It must be greater than 0. |
| Max Disk Space | The HDD allowance for recording, combined with the Max Record Time before it will wrap the recording. It must be greater than 0. The default value is 1 GB. |
The following validations will apply to the Recording Location field. An error/warning/info message will display underneath the input field.
-
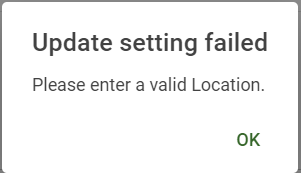
The below error will display if the Location is not entered:
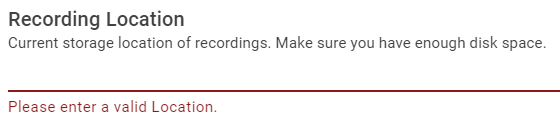
-
The below error will display if the directory does not exist.
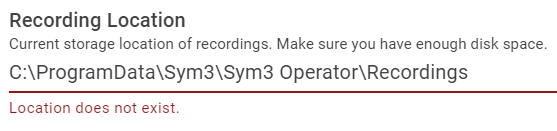
-
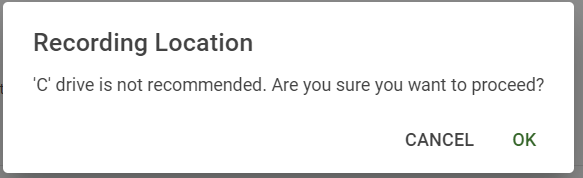
The below warning will display if the C drive is selected.
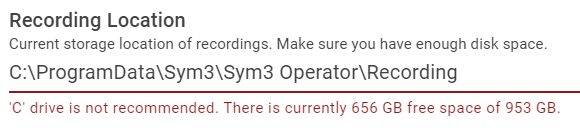
-
The below info about the disk space will display if the location is a valid directory.
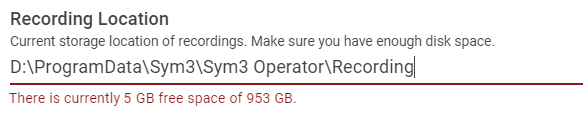
If any of the errors above is not cleared, when the Save button is clicked, a dialog with the error will pop up indicating the update of settings is failed.
If there’s no error but a warning from above is not cleared, when the Save button is clicked, a dialog with the warning will pop up requesting for confirmation.
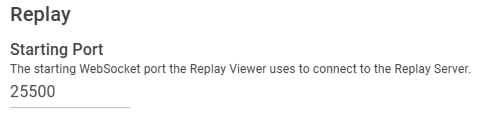
Replay
| Setting | Description |
|---|---|
| Starting Port | Default = 25500 A range of ports must be allowed in the firewall rules. Example: 25500, 255xx (255xx should be 25500 + number of maximum replay client allowed from the license) |
Note: Only secured websocket is provided.
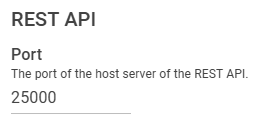
REST API
| Setting | Description |
|---|---|
| Port | Default = 25000 The port of the host server of the REST API. This port number must be allowed in the firewall rule on server side. |
Note: Only secured communication is provided.
Web Settings
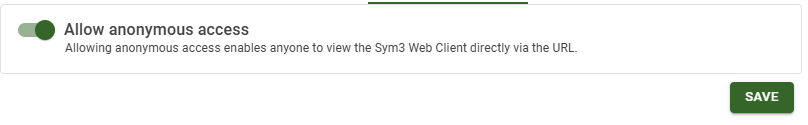
Web Client Settings
| Setting | Description |
|---|---|
| Anonymous Web Client access | Default = Disabled Enable the item to allow anonymous access to the web client page |
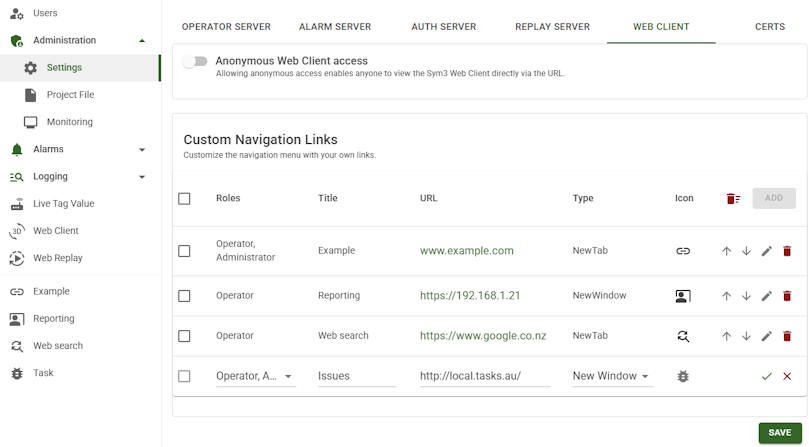
Custom Navigation Links
You can add custom navigation links to the Sym3 Web interface, allowing you to tailor the navigation menu to your organization’s needs. This feature makes it easy to provide users with quick access to important resources such as documentation, dashboards, or external systems.
| Setting | Description |
|---|---|
| Role | Specifies which user role(s) can see the navigation link. This ensures that only the appropriate audience has access to the link. |
| Title | The display name or label for the link, as it will appear in the navigation menu. |
| URL | The full address of the hyperlink. This can point to either an internal Sym3 Web page or an external site. |
| Type | Determines how the link opens: either in a new browser tab/window or within the current session. |
| Icon | An optional icon used to visually represent the link, making it easier for users to recognize at a glance. |
Certificate Management
To enable remote access (via a web browser from outside the server), an SSL certificate with the specified IP address or hostname is required. For detailed steps to apply a new certificate, see Enable Remote Access page in the ‘Setting Up’ section.
License Settings
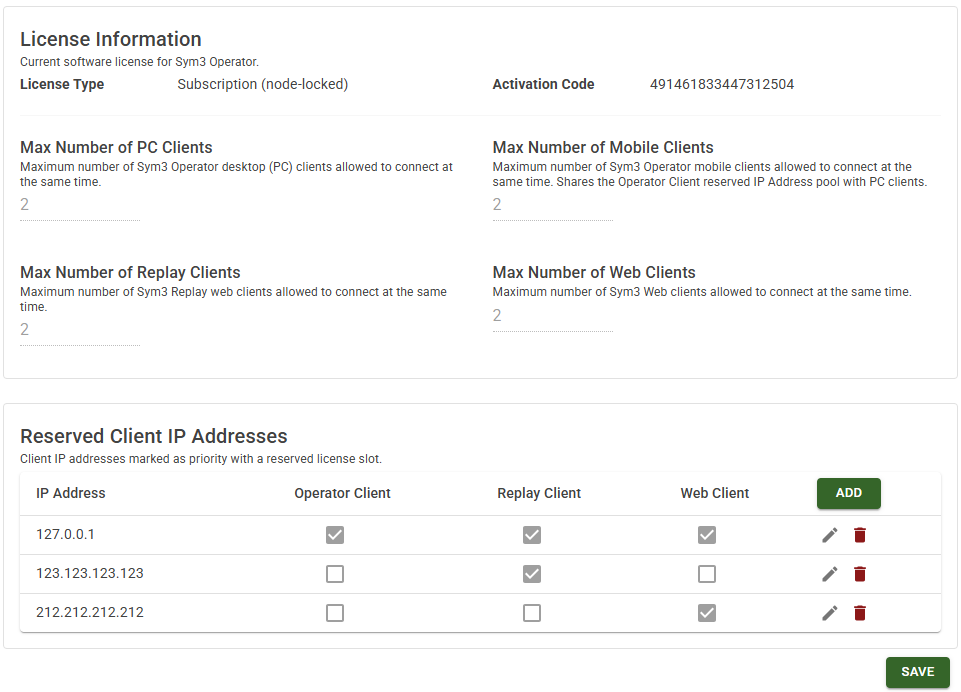
License Information
These settings provide a read-only overview of your current Sym3 licensing configuration and how client connections are controlled. They show the installed license type and its details. All of these values are informational only and cannot be edited from this screen; if license information or limits need to be changed, you must launch the Sym3 License Manager application.
| Setting | Description |
|---|---|
| License Type | Displays the type of Sym3 license installed. |
| Activation Code | Displays the activation code used to activate the current Sym3 license. |
| Max Number of PC Clients | Maximum number of Sym3 Operator desktop (PC) clients allowed to connect at the same time. |
| Max Number of Mobile Clients | Maximum number of Sym3 Operator mobile clients allowed to connect at the same time. Shares the Operator Client reserved IP Address pool with PC clients. |
| Max Number of Replay Clients | Maximum number of Sym3 Replay web clients allowed to connect at the same time. |
| Max Number of Web Clients | Maximum number of Sym3 Web clients allowed to connect at the same time. |
Reserved Client IP Addresses
License seats can be reserved for specific client IP addresses so that priority clients always have a guaranteed slot, while the remaining seats are available for other users.
Client VIP IP Addresses are IPs that always have a seat saved. If the Sym3 Operator license has 10 total seats and there are 3 VIP IPs configured, then:
- Up to 3 seats are reserved for those VIPs.
- Non-VIPs can use at most 10 − 3 seats.
- A VIP can still connect even when all non-VIP seats are taken (that’s the point of the reservation).
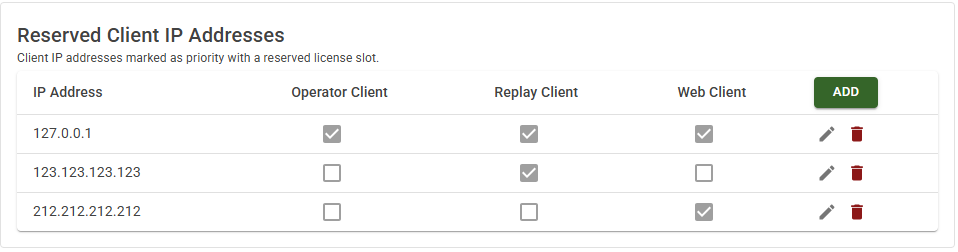
| Setting | Description |
|---|---|
| IP Addresses | Sym3 Web Client IP addresses marked as priority with a reserved license seat. |
| Operator Client | Select to reserve this IP Address license seat for Sym3 Operator Client. |
| Replay Client | Select to reserve this IP Address license seat for Sym3 Web Replay Client. |
| Web Client | Select to reserve this IP Address license seat for Sym3 Web Client. |